Avoid SoD violations and achieve smooth recertifications
Events
Join the largest event about Cybersecurity in Suisse Romande!
This year we will present also interactive workshops
In today's interconnected healthcare environment, the integration of medical devices requires a solid understanding of cybersecurity and data protection to ensure patient safety and regulatory compliance.
This webinar, Medical Devices meet Compliance, explores the critical intersection of device innovation and the evolving data security standards.
Designed for healthcare professionals, medical device manufacturers, regulatory compliance officers, IT security specialists, and healthcare administrators, this session will equip you with the knowledge needed to navigate complex regulatory frameworks and implement effective security measures:
- Participants will gain insights into the importance of safeguarding sensitive health information against cyber threats while navigating a complexity of regulations, including HIPAA, GDPR, the Federal Act on Data Protection, ISO standards, and industry-specific requirements.
- Attendees will learn practical strategies for achieving compliance, mitigating risks, and building trust in medical device technology amidst a rapidly changing regulatory environment.
ABOUT THE SPEAKERS:
- Mauro Verderosa is a recognized and certified cybersecurity expert with more than 20 years of experience in the field and the only ISC2 Official Trainer in Switzerland. He is specialized in Identity and Access Management and PAM, with 20+ year of experience in the domain. He joined some of the most important projects in Europe covering the design and implementation of complex solutions and architectures. Accustomed to working in highly regulated environments such as the financial, pharma and medical sector, he is also able to be the first point of contact in the communication between management and technicians. Mauro is also the Founder & President of the ISC2 Suisse Romande Chapter.
- Alexandra Medrea is a Risk Management & Cybersecurity expert in the medical device industry with proven experience leading risk management efforts, implementing ISO 14971 systems, and designing cybersecurity frameworks aligned with IEC 81001-5-1. She supports companies in embedding safety and cybersecurity into product development and compliance processes, helping teams strengthen practices, meet regulatory expectations, and protect patients while fostering innovation.
- Randle A. Henry has more than twenty years of hands-on functional as well as leadership experience evaluating and accessing cybersecurity in a broad range of IT environments and industries. He has consulted with Fortune 100 companies, small enterprises, and government entities alike on security, compliance, and risk and has performed and led framework and maturity assessments across hundreds of unique IT environments. He also performs cyber risk assessments, cybersecurity compliance assessments, vulnerability assessments and penetration tests to help companies improve their cybersecurity posture. This hands-on experience — combined with ongoing education and active certifications ensure Randle is at the forefront of best practices, leading frameworks (including COBIT, NIST 800:53, NIST-CSF, ISO, HIPAA, HITRUST, GDPR, SOC1/2, FEDRAMP, DFARS - over 40 total) and regulatory requirements (including Sarbanes-Oxley and PCI). Highly respected in his field, Randle has taught security auditing, business chemistry and ISO framework classes across the world for Deloitte's customer.
Join us on the 9th of October at 16:00 to deepen your understanding of the challenges and best practices at the convergence of medical device deployment and data security compliance.
NOTE: The webinar link will be sent to you closer to the event's date!
Join the largest event about Cybersecurity in Suisse Romande!
This year we will present also interactive workshops
Join PSYND and KnowBe4 to check-out on our Cyber Awareness Program, designed to meet essential compliance requirements and bolster your organization's cybersecurity posture.
This interactive session will cover critical topics such as phishing prevention, password management, data protection and incident response.
Participants will gain valuable insights into current cyber threats and industry best practices. By building a culture of security awareness, we empower employees to protect sensitive information and comply with regulatory standards. Don't miss this opportunity to enhance your cybersecurity knowledge! The webinar link will be shared via e-mail prior the event!!!
About the Speakers
Maria Bicsi has a strong background in pedagogy and psychology and almost for a decade she is working in the cybersecurity field with a deep knowledge in data protection, compliance, IAM&PAM and risk management. She is a PRINCE2 certified project manager leading several awareness programs to success. With her organized working methodology and customer-oriented approach she is able to guide you through the processes, plan exactly your activities and follow up on each of them, and to generate both operational and executive reports.
Paul Nkengue is a seasoned account executive at a leading cyber awareness company, leveraging his extensive background in business development and customer care to drive success. Fluent in several languages, he excels in building relationships with diverse clientele and understanding their unique needs. With 5+ years of experience in sales, he combines technical expertise with a passion for educating organizations on cybersecurity best practices. Paul's commitment to excellence and proactive approach make him a trusted partner in the ever-evolving digital landscape.
Following the success of the Swiss IT Forum and our two demonstrations, we are delighted to announce that we are organising, in partnership with BlackBerry and Ground Labs, a convivial fondue dinner at the Hôtel Les Armures on 22nd of November from 18h30 to 21h00.
This event will be a golden opportunity to meet and network with cybersecurity experts. Imagine chatting and exchanging ideas and experiences with renowned experts in the field of cyber security. And all this will take place in a luxurious atmosphere, conducive to lively conversation and friendly connections. So get ready for an exceptional evening of cybersecurity networking and enriching encounters!
Don't miss this opportunity to network and have a great time in the company of exciting people. Book your place now and get ready for an unforgettable experience!
Join the biggest event about Cybersecurity in Suisse Romande!
This year we will present also interactive workshops
Also this year we will be present at the Geneva technology show. If you are interested in cybersecurity, come and visit us, we have many surprises for you!
PSYND is inviting you to a Lunch & Learn Event with his partner BlackBerry!
We will be talking about how to protect your organization from advanced persistent threats (APTs) with regular compromise assessments and professional incident.
If you are the IT Manager or Security Responsible in the Geneva region, don't miss out this opportunity to listen to great presentations and to talk to the experts during an apero.
nFADP is entering into force on the 1st of September. Be prepared!
PSYND is inviting you to a Lunch & Learn series with its partnes to help your preparation to the nFADP compliance. The first event will take place at PSYND's offices in Geneva together with Backup ONE.
We will be talking about how to properly backup up your data, how to test and verify the backup to make sure everything works in case of an emergency.
You will receive a compact insight on how to backup, validate and restore data to make sure, your business can recover as fast as possible.
If you are the IT Manager or Security Responsible for an SME in the Geneva region, don't miss out this opportunity to talk to the experts.
During this session, Samuel Lopez will go through 5 important items needed to be handled as part of a IGA program rollout, those items have to be accomplished at different timelines, in alignment with the program maturity. They will be precisely explained and with practical examples to get some clear takeaways from the session. In the second part Mauro Verderosa will highlight the key components and success factors of a Privileged Access Management project.
ABOUT THE SPEAKERS
- Samuel López is a cybersecurity professional passionate about the Identity and access management subjects. During his professional career in Holcim, he worked several years in the directories management and hardening, being awarded by Microsoft as Most Value. After leading the directory services team more than 3 years, Samuel accepted the challenge to Lead the User lifecycle team for the EMEA Region, with the clear ambitions to maximize the business value proposition and to improve the security posture around the digital identities management.
- Mauro Verderosa (CEO PSYND, Founder of the Swiss CyberSecurity Association, President of the (ISC)² Suisse Romande Chapter). Authorized (ISC)² Trainer, CISSP and CCSP certified, Cybersecurity Specialist and IAM Expert: developed many years of experience with some of the most important IAM products. Experienced as a Cybersecurity integrator, solution architect, business analyst technical project manager, data protection expert. Senior Trainer for Cybersecurity courses, IAM architectures, IAM process design, and best practices.
Mária Bicsi is opening the doors for the Zero-Day Conference that will be held on the 20th of October 2022 in Geneva.
This is the largest Cybersecurity conference in Switzerland grouping the most important Swiss companies that will inspire you with their strategies for 2023.
For more information: https://www.zero-day.ch/
Also this year we will be present at the Geneva technology show. If you are interested in cybersecurity, come and visit us, we have many surprises for you!
Join us on the 22nd of June at 11:30 CET and learn why a CISSP it's so important for all the experienced cyber security professionals
We prepared a special offer for the webinar attendees!!! Stay tuned!
Learn how to effectively prevent data leakage and mitigate the risk of insider threats with Enterprise DLP.
Real use cases will help you understand the role of enterprise DLP in regulatory compliance (e.g. ISO standards or data protection regulations).
Using examples from the verticals like banking, audit, tax & accounting consulting we will explain how Safetica ONE helped companies to:
- discover what kind of sensitive data they have in their environment
- where they reside
- which flows could prevent leakage of sensitive or confidential information using unified content & context classification
- prevent security risks and audit employee's activities
Ransomware moves through IT networks looking for vulnerabilities across the network but especially in backups as they are critical to recovery plans. By destroying or damaging backups, attackers have a higher chance of getting their ransom demands paid. That's why the attacks can be so devastating.
Come and join us in this webinar to learn from the experts the best practices about how to protect your backup systems and other critical IT infrastructure to make sure you stay in control.
Main speakers:
- Daniel Caduff, from the Swiss Federal Office for National Economic Supply
- Mária Bicsi, from PSYND
- Niels Vlastra, from Osirium
80% of companies suffer data loss through empoyee errors or malicious acts. You can run your company without risking the loss of valuable regulated data or business-sensitive information like contracts, blueprints, or source codes.
Employees are an important part of a cybersecurity system but most experts see them as the weakest link. To successfully protect an organization we need a human firewall but to create it we need conscious users armed with the main tool: knowledge. They should know how to recognize attacks and how to react to them. That’s why we should concentrate on building within the organization's culture of enablement rather than a culture of fear. Employees should feel that they are the strong link. We will be speaking about compliance and regulation requirements, and in which way we can be aligned as companies to those if we complete a cybersecurity awareness program. On the other hand we will be presenting industry best practices and hands-on advice on how to build a strong cybersecurity culture.
L’Evénement Connecté (le LEC) a pu se dérouler à nouveau en présentiel, les 21 et 22 septembre à Genève. Avec un programme riche de conférences et tables rondes. Focus sur trois d’entre elles, dédiées à la cybersécurité, à la transformation digitale et à la disruption
La tendance à s'orienter vers le cloud semble être une évolution naturelle des services informatiques des entreprises, mais en réalité, derrière cette transformation, il est essentiel de faire une analyse interne de la manière dont les anciens processus doivent être adaptés au cloud, garantissant la même qualité de services et en même temps la sécurité des systèmes et des données. Nous découvrons dans ce panel les éléments clés essentiels à prendre en compte pour une stratégie cloud solide.
Risk-based authentication both enhances security and user experience by allowing you to rank the resources you want to protect based on risk level and type of user. This gives you the power to create rules that are unique to the security structure in your organization, therefore enabling more flexibility or higher protection only when necessary.Join our session on June 8th with Alexandre Cagnoni, Director of Authentication at WatchGuard Technologies, and learn about the powerful connection between zero-trust adoption and risk policies, and how multi-factor authentication sits at the core of these approaches by bringing the technology and so very needed today to protect user identities and Cloud applications.
- Why Risk-Based Authentication?
- Multi-Factor Authentication and Risk Intelligence: Optimized User Management
- Risk Policies Prevent Breaches There Can’t Be Zero-Trust Without MFA
- Using MFA and Risk Policies in Your Zero-Trust Deployment
- Business Risk Assessment Guide
SPEAKERS:
- Mauro Verderosa - Cybersecurity Expert | PSYND
- Alexandre Cagnoni - Director of Authentication | WatchGuard Technologies
.. And How to Stop Them!
Microsoft Office 365 has been the primary enterprise productivity suite for years, starting on traditional endpoints and mobile devices.
About this Event
Then came the pandemic-driven tectonic shift to remote working. Making the Office suite - from Outlook to Teams - a requirement for mobile devices. But it also created risks that may not be immediately obvious.
Register to watch our on-demand webinar, in which our experts' OUTLINE:
- The top four threats that can undermine your O365 implementation on mobile devices;
- How to prevent attacks on corporate devices; and
- How to respond to attacks on personal (BYO) devices without impacting privacy.
SPEAKERS:
- Mauro Verderosa - Cybersecurity Expert | PSYND
- Ashish Patel - GM, EMEA | Zimperium
- Sergej Straub - Director Technical Sale | Zimperium
Privileged Access Management (PAM) is critical for good cybersecurity, and if you don’t have PAM in place, all your systems are vulnerable.
But many organizations are yet to implement PAM. That could be for many reasons: traditional PAM solutions have been complicated, expensive, and could get in the way of admins trying to get their work done. But that’s no longer the case with a modern PAM solution like that from Osirium.
During this event Alex Breedon, from GibTelecom, and Mauro Verderosa, from PSYND will show why companies should speed up their adoption of PAM.
Join our live event at 16:30 CET
Getting under the skin: the Social Engineering techniques
In a world where the cybersecurity applications are day after day more protected and solid, the most malicious attackers decide to target the weakest ring of system: the human.
Through this presentation we will discover what are the social engineering attacks, how they are defined, how they are performed and how they can be identified before the attacker might be able to gain the access to the most sensitive information.
With an exploding set of cloud infrastructure services and an increasing number of stakeholders involved in infrastructure and security decisions, the cloud has formed the perfect storm for security. In order to gain the benefits of the cloud and meet business objectives, cloud security needs to be made less complex.
Business requirements and DevOps processes demand faster application delivery, however, if you increase the speed of delivery, everything else must follow suit. For example, compliance, which changes based on industry, geography, and infrastructure, as well as protecting against evolving and increasingly sophisticated threat vectors.
Trend Micro and PSYND shows you, how you secures the different parts of your environment within one simple platform.
To attend to this event it's mandatatory to register:
Join with us the Veracode virtual summit for 2020. Learn which are the benefits of secure coding and learn best practices.
DevSecOps Done Right
Debunking the AppSec Silver Bullet Myth
AppSec Beyond Technology
Fix What You Find With Developer Engagement
Panel Discussion - AppSec in Practice
PSYND is participating to the Swiss Cybersecurity Days 2020.
Visit us at stand #119.
PSYND is hosting the first (ISC)² Chapter Suisse Romande kick-off meeting.
Mauro Verderosa presents the key benefits of a PAM solution on the (ISC)² Chapter Switzerland event.
PAM solutions are rapidly entering all companies by strengthening existing systems and architectures. These solutions should be seen not only as a cost, but also as an investment. Let's find out what are the befits of such solutions, followed by a demo.
Join the biggest event about Cybersecurity in Suisse Romande
Mária speaks in Miami about Governamental Security.
Open source software risks revolve around three key areas: visibility, security, and governance. In this session we will help you understand these factors and how to formulate a stronger cybersecurity strategy that protects you from open source risk.
Join us for this live webinar organized by PSYND to learn how Veracode can help you gain visibility of open source risk and formulate a stronger cybersecurity strategy that protects you from related cyber attacks.
Mária presents about how to build a Cybersecurity community at the Romanian parlament.
The WSIS Forum is a global multi-stakeholder platform facilitating the implementation of the WSIS Action Lines for advancing sustainable development. The Forum provides an opportunity for information exchange, knowledge creation and sharing of best practices, while identifying emerging trends and fostering partnerships, taking into account the evolving Information and Knowledge Societies.
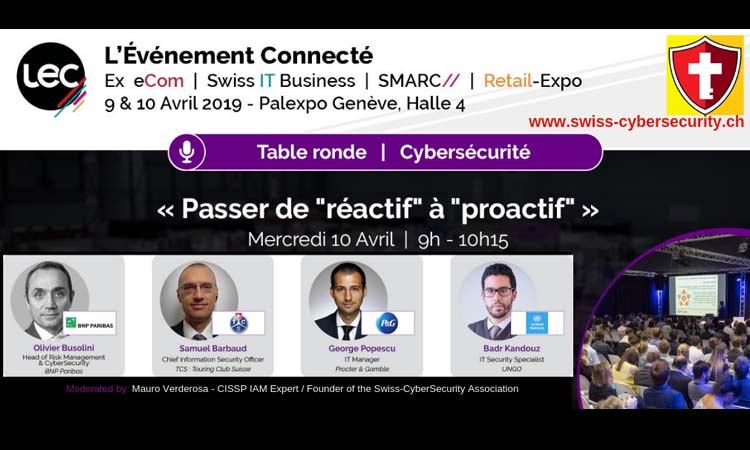
Palexpo, Mercredi 10 Avril | 9h - 10h15 | Salle A
En partenariat avec l'association Swiss-Cybersecurity - Modérateur Mauro Verderosa (Responsable)
Experts et spécialistes en cybersécurité partageront leur expérience lors de cette table ronde. Nous verrons comment les entreprises préparent leur stratégie de cybersécurité et comment ils la mettent en œuvre. Outre les aspects technologiques, des aspects relatifs au leadership, à la gestion et à la planification stratégique seront également abordés.
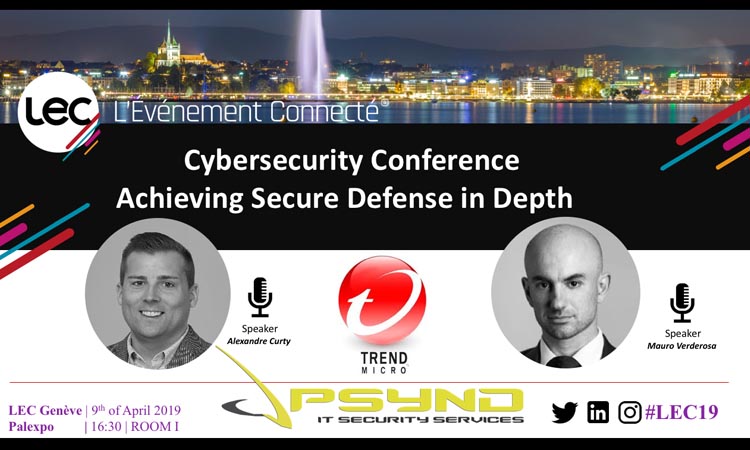
Palexpo, Tuesday 9th of April | 16:30 - 17h15 | Room I
Every day we listen about new attacks, passwords stolen and data loss: are we really doing everything necessary to protect them?
Join our workshop: with Alexandre Curty (Trend Micro) and Mauro Verderosa (PSYND), we will go through different scenarios and we will both discover how to recover from an attack and how to prevent them from happening.
Mária presented Privileged Access Management in the Western-European Public-Private Dialog Platform conference.
The conference was held in Porrentruy on the 29th and 30th of November 2018.
Mária presented a Cybersecurity Awareness Training about how to protect your private life.
You will understand how many information your smartphone is releasing every day. How secure your credit cards, how to secure your MacBook and how to get complete isolation of signals when you want to protect your privacy.
Join the biggest event about Cybersecurity in Suisse Romande
Zero-Day is a conference aiming to share knowledge, to develop leadership skills, to deepen the expertise in the cybersecurity field, and to discover innovative cyber-defense solutions to protect your assets. The conference gives you a great opportunity to meet your fellows and to exchange ideas with highly skilled cybersecurity professionals. We are providing you with a full-day agenda, including presentations and practical workshops that might be supporting your company to improve your Cybersecurity Strategy. The 18 speakers will be covering 4 sections: Network Security with AI, Infrastructure Security, Strategic Planning and Governance and Data Protection.
Mauro Verderosa presented the IAM evolutions in the cloud domain on the (ISC)² Chapter Switzerland event.
In the latest years companies are migrating their systems on premise to cloud solutions. Before this transformation takes place, it's needed to run a deep analysis to be sure that processes and internal policies are respected. Moreover, the security is playing a key factor because, without the needed protection, business confidential information could be wrongly exposed to Internet generating a data loss that could compromise the business of a company. Discover what measures should be implemented to enforce the access control in the cloud and what are the key points that should be considered before developing a secure infrastructure.
Mauro Verderosa will present CA PAM, the Computer Associates solution for PAM.
The presentation will introduce all the main concepts of what a PAM solution should have, from the Session Monitoring to the Segregation of Duties. All these concepts will be explained with practical examples showing how the product is addressing all the features.
PSYND and Swiss-CyberSecurity listed by the Cybersecurity Observatory.
Mauro Verderosa will present at the Emergency Forum the top cyber-threats foreseen for 2019. In this section will be discussed what are the current attacks and how they could evolve in the coming months.
Come and visit PSYND at stand IT04 in Palexpo: Mária, Petra, Camille and Guillaume will present you how IAM could help your business and improve the security in your company and we will also introduce you about how initiative with Swiss-CyberSecurity.
Patrick and Robert , from One Identity, will show you the unique value of One Identity as an IAM market leader in Europe.
Don't miss our public presentation about new trends in IAM on the 24th of April at 15:00 in the room H.
The Swiss IT Business exhibition and its collocated event, the Bi Swiss Forum Geneva, is the largest professional gathering dedicated to business software and IT solutions in French-Speaking Switzerland. The 6th edition will take place on April 24-25, 2018. 4,000 trade visitors will meet 250 companies (75% Swiss, 25% foreign) and will attend 120 themed conferences, keynotes and workshops.
The exhibition offers to its trade visitors a rich and varied program of themed conferences, an exhibition area, workshops, business meetings and training sessions.
Psynd is inviting you to be part of it. For more details about the topic and the invitations please contact us.
Automation and innovation are now key enablers to improve access control whether it be from a business, technical or compliance perspective (GDPR).This conference aims to provide CIOs, CISOs and business decision makers with insights into the latest developments of identity and access management, including the protection of the privileged accounts.
Automation and innovation are now key enablers to improve access control whether it be from a business, technical or compliance perspective (GDPR).
This conference aims to provide CIOs, CISOs and business decision makers with insights into the latest developments of identity and access management, including the protection of the privileged accounts.
You can gain 4 CPEs for your (ISC)² certification.
We will present you Identity & Access Management tools:
o How you can manage internally the systems of your company and how you can enforce your compliance and audit
o How to manage globally the password in your system and how to implement a Privileged Password policy
o How to protect your system using a Cyber AI tool
Christian Folini, Matteo Mazzeri and Mauro Verderosa will present at the Swiss-CyberSecurity event Open Source Security.
The event is organized by PSYND. You can gain 2 CPEs for your (ISC)² certification.
Mária presented a Cybersecurity Awareness Training at Women in Digital Geneva.
Michel Paschalides and Omar Benjumea will present at the Swiss-CyberSecurity event what are the most common Ransomware and you will receive a high-level introduction to the concept of ransomware and then dig deeply into the methods you would take to protect yourself from this scourge.
The event is organized by PSYND. You can gain 2 CPEs for your (ISC)² certification.
PSYND is sponsor and organizer for the Swiss-CyberSecurity.ch events.
In this video Mária is presenting the Annual Initiative for 2018.
Best wishes from our community to our members. In 2017 Swiss-CyberSecurity.ch organized 20 events and 9 of them were conferences with professional speakers.
Come and visit our stand and get a free juice or some fruits!
Mike Kalomeni and Kay Addai will present at the Swiss-CyberSecurity event what is what is an ICOs, what are the opportunities around them, but also what are the risks. Event organized by PSYND. You can gain 2 CPEs for your (ISC)² certification.
Mauro Verderosa and Mária Bicsi join the team of Hidora to participate to the Hackaton of Geneva 2017.
The final result will be the 2nd position!
Mauro Verderosa speaks in Geneva about Logical Access Control in the Swiss-CyberSecurity event organized by PSYND. You can gain 2 CPEs for your (ISC)² certification.
Mauro Verderosa speaks in Geneva about Physical Access Control in the Swiss-CyberSecurity event organized by PSYND. You can gain 2 CPEs for your (ISC)² certification.
At the Gartner Security & Risk Management Summit you’ll learn how to use proven practices as well as innovative technologies and methods to help manage increasing cybersecurity risks without unnecessarily inhibiting the business.
Mária Bicsi speaks in Geneva about GDPR in the Swiss-CyberSecurity event.
Mauro Verderosa from PSYND speaks in Zurich about Social Engineering on the Swiss Hacking Day 2017 organized by SIGS.
While day after day the technology is improving and the systems are always more secure, the weakest ring of the security chain is the human factor. Understand what is a Social Engineering attack, how it is developed, how to recognize it and how it can be prevented.
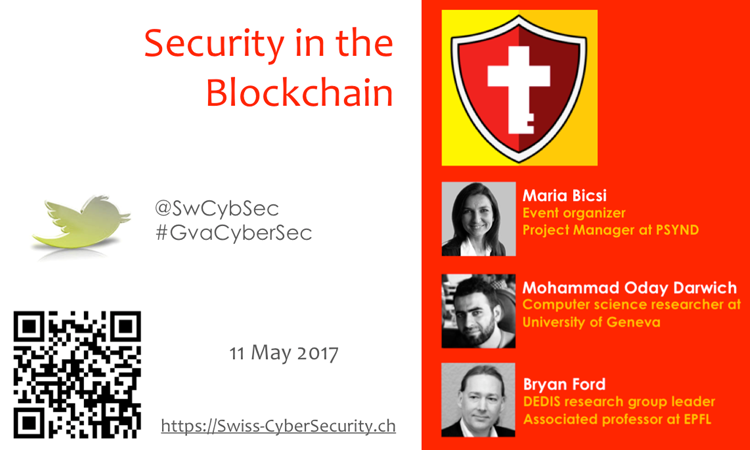
Discover the Blockchain from the security point of view. The introduction will be given by Oday Darwich, researcher and teacher assistant at Geneva University, about Blockchain and Ethereum. We will dive deeper in the Blockchain Security with Prof. Bryan Ford, who leads the Decentralized/Distributed Systems (DEDIS) research group at the Swiss Federal Institute of Technology in Lausanne (EPFL).
Mauro Verderosa speaks about Security in IoT in the Swiss-CyberSecurity event.
PSYND organize with ThinkYoung, a Swiss organization focused on young people, a full day workshop in Georgia.
Mauro Verderosa speaks in Geneva in the Risk Management event organized by PSYND.
Mauro Verderosa speaks in Geneva in the Cybersecurity awareness event organized by PSYND.
Mauro Verderosa speaks in Geneva in the Cybersecurity awareness event organized by PSYND.